The Hacker News: Dark Web Malware Logs Expose 3,300 Users Linked to Child Abuse Sites
An analysis of information-stealing malware logs published on the dark web has led to the discovery of thousands of consumers of child sexual abuse material (CSAM), indicating how such information could be used to combat serious crimes.
Jul 25
"Approximately 3,300 unique users were found with accounts on known CSAM sources," Recorded Future said in a proof-of-concept (PoC) report published last week. "A notable 4.2% had credentials for multiple sources, suggesting a higher likelihood of criminal behavior."
Over the past few years, off-the-shelf info-stealer variants have become a pervasive and ubiquitous threat targeting various operating systems with an aim to siphon sensitive information such as credentials, cryptocurrency wallets, payment card data, and screenshots.
This is evidenced in the rise of new stealer malware strains such as Kematian Stealer, Neptune Stealer, 0bj3ctivity, Poseidon (formerly RodStealer), Satanstealer, and StrelaStealer.
This is evidenced in the rise of new stealer malware strains such as Kematian Stealer, Neptune Stealer, 0bj3ctivity, Poseidon (formerly RodStealer), Satanstealer, and StrelaStealer.
Distributed via phishing, spam campaigns, cracked software, fake update websites, SEO poisoning, and malvertising, data harvested using such programs typically find their way onto the dark web in the form of stealer logs from where they are purchased by other cybercriminals to further their schemes.
"Employees regularly save corporate credentials on personal devices or access personal resources on organizational devices, increasing the risk of infection," Flare noted in a report last July.
"A complex ecosystem exists in which malware-as-a-service (MaaS) vendors sell info-stealer malware on illicit Telegram channels, threat actors distribute it through fake cracked software or phishing emails, and they then sell infected device logs on specialized dark web marketplaces."
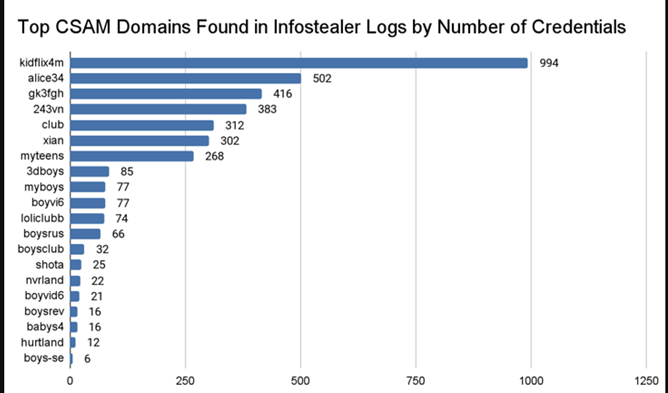
Recorded Future's Insikt Group said it was able to identify 3,324 unique credentials used to access known CSAM domains between February 2021 and February 2024, using them to unmask three individuals who have been found to maintain accounts at no less than four websites.
The fact that stealer logs also comprise cryptocurrency wallet addresses means they could be used to determine if the addresses have been used to procure CSAM and other harmful material.
Furthermore, countries like Brazil, India, and the U.S. had the highest counts of users with credentials to known CSAM communities, although the company said that it could be due to an "overrepresentation due to dataset sourcing."
"Info-stealer malware and stolen credentials are projected to remain a cornerstone of the cybercriminal economy due to the high demand by threat actors seeking initial access to targets," it said, adding it has shared its findings with law enforcement.
"Info-stealer logs can be used by investigators and law enforcement partners to track child exploitation on the dark web and provide insight into a part of the dark web that is especially difficult to trace."
Get in touch
-
admin@inv-network.org
About Us
Inv-Network was created to support those who are tasked with the difficult job of protecting children from online child exploitation. Our goal is to provide community, resources, and training to Law Enforcement, District Attorney's, and Parole & Probation Officers.
Copyright © 2023
SEX OFFENDER MANAGEMENT SYMPOSIUM REFUND POLICY
Our Symposium aims to provide the most beneficial and practical experiences for our students. From providing resources, special guest speakers, and also networking and bonding experiences. All of this is costs for us at Intellect-LE. We do our best to cover the travel costs for our instructors as well as resource give aways for students and all of that is paid prior to the course dates. If we have a large amount of students cancel before class, this incurs a large out of pocket expense for use and we would not be able to sustain our course. When you or your agency registers and pays for class we believe you are attending. We understand that circumstances arise so while we do not refund paid seats, we do offer the following options;
1. Your seat may be transferred to another attendee from your agency at no additional cost.
2. Your seat may be moved to our next available training date, even if it is in another location.
3. You can be granted 1 year's worth of access to our skills center and all the training it contains.
1. Your seat may be transferred to another attendee from your agency at no additional cost.
2. Your seat may be moved to our next available training date, even if it is in another location.
3. You can be granted 1 year's worth of access to our skills center and all the training it contains.
SEX OFFENDER MANAGEMENT SYMPOSIUM REFUND POLICY
Our Symposium aims to provide the most beneficial and practical experiences for our students. From providing resources, special guest speakers, and also networking and bonding experiences. All of this is costs for us at Intellect-LE. We do our best to cover the travel costs for our instructors as well as resource give aways for students and all of that is paid prior to the course dates. If we have a large amount of students cancel before class, this incurs a large out of pocket expense for use and we would not be able to sustain our course. When you or your agency registers and pays for class we believe you are attending. We understand that circumstances arise so while we do not refund paid seats, we do offer the following options;
1. Your seat may be transferred to another attendee from your agency at no additional cost.
2. Your seat may be moved to our next available training date, even if it is in another location.
3. You can be granted 1 year's worth of access to our skills center and all the training it contains.